Over the last two decades, numerous high-profile data breaches rocked the business world. The conventional castle-and-moat model that relied heavily on VPN made most businesses vulnerable to external attacks.
In 2010, John Kindervag, a former Forrester analyst, introduced the Zero Trust Security model. Soon after, tech behemoths like Google and Akamai adopted zero-trust principles internally, eventually paving the way for commercially available zero-trust solutions.
The adoption of the zero trust model accelerated during COVID-19 when businesses went remote and security risks shot up exponentially.
What is a Zero Trust Model?
The Zero Trust Security Model, also known as Zero Trust Architecture (ZTA), Zero Trust Network Access (ZTNA), or Perimeterless Security, is a multi-checks strategy for securing IT systems.
It works on the Never Trust, Always Verify approach and doesn’t trust any entity by default. The entity could be a user, app, service or device.
Based on the principle of least-privileged access, Zero Trust Architecture or ZTA enforces strong identity verification. For every new connection, this trust is continually reassessed, even if the entity was authenticated beforehand. It validates device compliance and grants the least privileged access to only explicitly authorized resources.
The concept is still constantly evolving, maturing, and gaining traction.
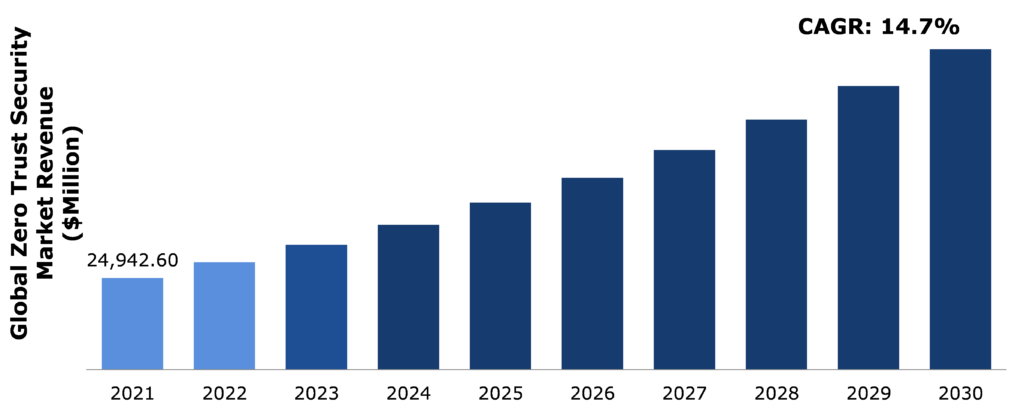
Why Zero Trust Is A Must For Modern Networks?
A decade back, most enterprise employees worked on site and only a handful required remote access. But, these days many employees need remote access and enterprises need to support remote access at a massive scale, which maximizes the risks associated with VPN.
The perimeter-based model was designed specifically for on-premises corporate data centers. Now, the resources of most enterprises remain scattered across private data centers and numerous clouds, disseminating the traditional perimeter.
Most modern corporate networks have multiple interconnected zones, cloud services, and infrastructure, connections to remote and mobile environments, and connections to non-conventional IT, such as IoT devices.
Zero trust implies that the traditional method of trusting users and devices within a supposed “corporate perimeter”, or those connected via a VPN, is not sufficient for the complex environment of a corporate network.
The zero-trust approach promotes mutual authentication. It verifies the identity, and integrity of users, devices and their location. Once it confirms the device identity, health and user authentication, it grants access to applications and services.

Zero trust principles can be applied to both data access and data management. To implement maximum security, every single request to access data is dynamically authenticated, ensuring the least privileged access to resources. Attribute-Based Access Control (ABAC) enables the administrator to apply policies based on data attributes, user identity, and environment type.
How is Zero Trust Security Different from the Traditional Approach?
Historically, enterprises counted on a castle-and-moat cybersecurity model, where anyone outside the corporate network perimeter was viewed with suspicion, while those inside were trusted. This practice, implicit trust, assumed that internal users were inherently trustworthy.
Enterprises depended heavily upon technologies like firewalls to secure corporate networks. An off-site user could remotely access the resources by logging into a VPN, a secure virtual tunnel into the network. However, problems arose when VPN login credentials were compromised, as was exposed in the infamous Colonial Pipeline data breach.
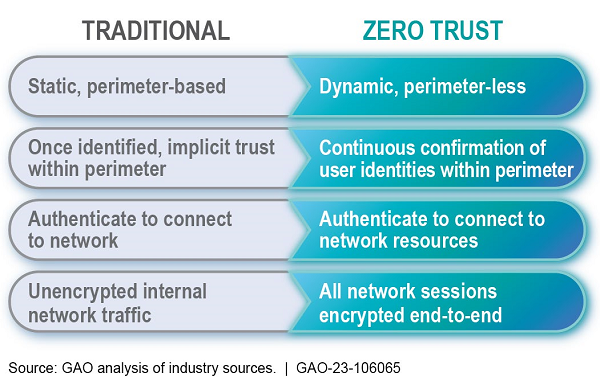
Once the perimeter was breached, the attacker could move laterally throughout the network.
Rather than focusing on user and device locations respective to the perimeter, whether inside or outside the private network, the zero-trust model grants access to information based on users’ roles and identities. The user could be anywhere: office, home, or elsewhere.
These measures are applied continuously throughout the network. They restrict lateral movement between applications, services, and systems, addressing insider threats and the potential compromise of legitimate accounts.
Benefits of Zero Trust Adoption for Enterprises
Here are some key advantages enterprises can enjoy by adopting zero-trust security:
- Enhanced Security: By granting the least privilege to employees, the zero trust model decreases the number of access points reducing the attack surface in turn. This makes it harder for hackers to breach systems. The impact of one compromised account is significantly redacted.
- Improved Data Protection: Verified users and devices are unlikely to be breached.
- Empowered Remote Workforce: The location-agnostic approach allows secure access for employees working from anywhere.
- Simplified Compliance: With practices like least privilege access and continuous verification that comply with data security regulations, compliance becomes easier.
- Reduced Costs: The initial investment required to implement zero trust is offset by the large amounts saved in penalties and remedial costs in the event of a data breach.
- Greater Visibility and Control: The centralized view of user activities and access patterns allows enterprises to identify suspicious behavior faster and take corrective measures.

What are the Key Elements of Zero Trust Security?
Three core principles guide zero trust security.
- Least Privilege Access: This principle controls how access and permissions are granted to users and devices. It allows minimal access for an employee to perform their tasks. The permissions are promptly removed once the task is done. For instance, a marketing employee might have access to customer data for analysis, but wouldn’t have the permission to modify financial records.
- Continuous Verification: Zero trust constantly re-evaluates every user and device trying to access resources instead of relying on a single sign-in. The common measures taken for continuous verification are:
- Multi-factor Authentication (MFA): Adding an extra layer of security beyond just a password.
- Device Health Checks: Ensuring devices are up-to-date with security patches and software updates.
- Contextual Factors: Considering location, time of day, and the application being accessed to assess risk.
- Never Trust, Always Verify: Every connection is treated as hostile and is verified through a step-by-step thorough verification before granting access.
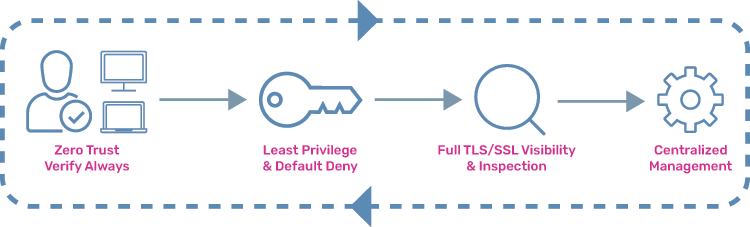
How to Get Started with Zero Trust?
Step 1. Assessment
- Identify Assets: Catalog all the valuable data, applications, and systems within your organization that require protection.
- Evaluate User Access: Understand the current access patterns and permission levels.
Step 2. Planning
- Define User Roles: Define user roles and identify the resources required to perform such roles successfully.
- Prioritize Implementation: Identify the areas where you want to prioritize zero trust first depending on your risk profile and available resources.
Step 3. Implementation
- Enforce Least Privilege: Grant users access to only the resources they need to perform their immediate roles.
- Enable Multi-Factor Authentication (MFA): Enforce multiple layers of verification like password, time-based OTP, and biometric verification.
- Network segmentation: Divide your network into smaller zones to limit lateral movement within the network in case of a breach.
Step 4. Monitoring and Improvement
- Continuous Monitoring: Establish a monitoring mechanism to keep a tap on user activity, device health, and access attempts. Track and counter anomalies faster.
- Refine Policies: Refine your zero trust policies as your understanding of access patterns and threats evolves.
Zero Trust Network Access
In a ZTNA, a central controller enforces the access policies set up by the organization. Only authorized users can attempt to connect to specific applications.
The ZTNA verifies users based on various factors:
- Who they are (identity)
- What their role is (permissions)
- What device they’re using (security posture)
- When they’re trying to access (time of day)
- Where they’re connecting from (location)
- What data they’re trying to access (sensitivity)
Access can be denied by ZTNA if any combination of these factors seems suspicious. For instance, if someone tries to access sensitive data at 3 am from an unknown location, it might be sufficient cause for the network controller to deny access. Users can only see the specific apps they’re allowed to use.
Have you applied to the Zero Trust Model yet? Share in the comments.
Subscribe to our blog for more info.